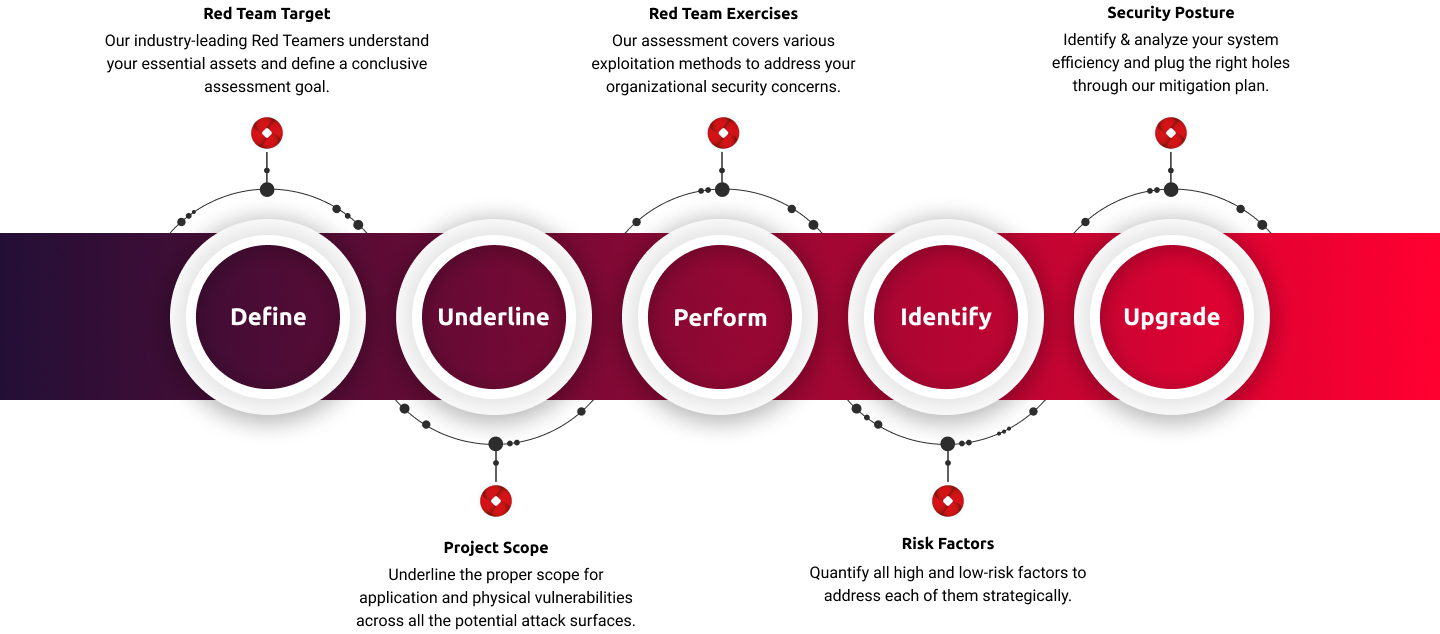
A Red Team Assessment’s goals include simulating actual attacks, verifying that the appropriate security controls have been put in place and are functioning, and identifying security flaws. Know Your Own Network, Systems, and Risk Level.
- Understand if your organization can prevent and detect real-life cyber-attacks.
- Understand your own systems, network, and risk level.
- Optimise existing security controls to maximise protection level.
- Highlight external and internal security gaps.
Identify Risks and Vulnerabilities Before Threats are Escalated.
- Completed picture from certified analysts.
- Analysis of attack simulation vs current state of prevention & detection controls.
- Based on industry leading standards and the latest attack techniques.
- Embed a continuous governance model to ensure improvement.
Expert Analysts
- Industry best certifications.
- OSCP, GPEN, GWAPT, CEH & more.
- Tailored approach.
Effective Postattack Cleanup
Following simulated attacks, put in place the right processes for effective mitigation against future attacks.
Our Red Team
Through the use of a mock opponent, our Red Team puts a system or an organization to the test. This is done to find security flaws that are frequently hidden from organizational insiders.
Risk Analysis
Risk analysis is the process of identifying and analyzing potential issues that could negatively impact key business initiatives or projects
With the same tools and permissions, we imitate an internal employee’s actions in this assault with the goal of gaining unauthorized access to sensitive IT systems, Active Directory, and business-sensitive applications and databases. Find out which computers, servers, and data are accessible, and whether an attack on the computer would allow it to migrate laterally throughout the organization.




